Let’s start with a basic two dimensional plot. Create the data file (uw.dat).
1 2 3 4 5 6 7 8 9 10 | |
Create the plot configuration file (uw.config).
1 2 3 | |
Now, plot using gnuplot uw.config.
Draw an Arrow
To draw and arrow from (3,2) to (6,8), use set arrow from 3,2 to 6,8. To specify end coordinate relative to the starting use rto instead to. e.g. set arrow from 3,2 rto 1,1.
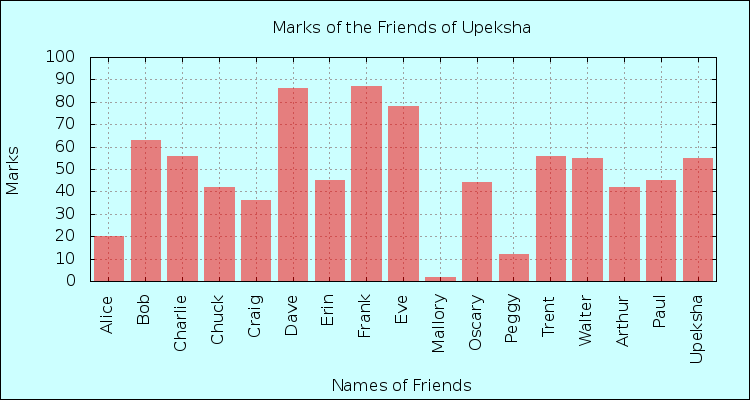
Plotting the Exam Results of My Friends
These are the marks taken by each of the friends. Format: Name, Marks.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | |
A brief description of each of the friends
Alice and Bob. Generally, Alice wants to send a message to Bob. Carol, Carlos or Charlie, as a third participant in communications.
Chuck, as a third participant usually of malicious intent.
Craig, the password cracker (usually encountered in situations with stored hashed/salted passwords).
Dan or Dave, a fourth participant. Erin, a fifth participant. (It’s rare to see Erin; E is usually reserved for Eve.) Frank, a sixth participant (and so on alphabetically).
Eve, an eavesdropper, is usually a passive attacker. While she can listen in on messages between Alice and Bob, she cannot modify them. In quantum cryptography, Eve may also represent the environment.
Mallet or Mallory, a malicious attacker (less commonly called Trudy, an intruder.); unlike the passive Eve, this one is the active man-in-the-middle attacker who can modify messages, substitute his/her own messages, replay old messages, and so on. The difficulty of securing a system against Mallet/Mallory is much greater than against Eve.
Oscar, an opponent, similar to Mallet/Mallory but not necessarily malicious. Could be white-hat but still wants to crack, modify, substitute, or replay messages. Peggy, a prover, and Victor, a verifier, often must interact in some way to show that the intended transaction has actually taken place. They are often found in zero-knowledge proofs. Trent, a trusted arbitrator, is some kind of neutral third party, whose exact role varies with the protocol under discussion.
Walter, a warden, may be needed to guard Alice and Bob in some respect, depending on the protocol being discussed. Arthur and Merlin: In interactive proof systems, the prover has unbounded computational ability and is hence associated with Merlin, the powerful wizard. He claims the truth of a statement, and Arthur, the wise king, questions him to verify the claim.
Paul and Carole. The characters were introduced in the solution of the Twenty Questions problem
Source: This list is drawn mostly from the book Applied Cryptography by Bruce Schneier. Alice and Bob are archetypes in cryptography; Eve is also common. Names further down the alphabet are less common. Read More
Now you know most of my friends, Let’s create the plot config file.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | |
Run gnuplot marks.config.
Despite gnuplot’s name, it is not part of or related to the GNU Project, nor does it use the GNU General Public License. You should always use simple ‘g’: ‘gnuplot’.